ThreatDown introduces auto-isolation
ThreatDown is the first security solution that offers three methods of auto-isolation.
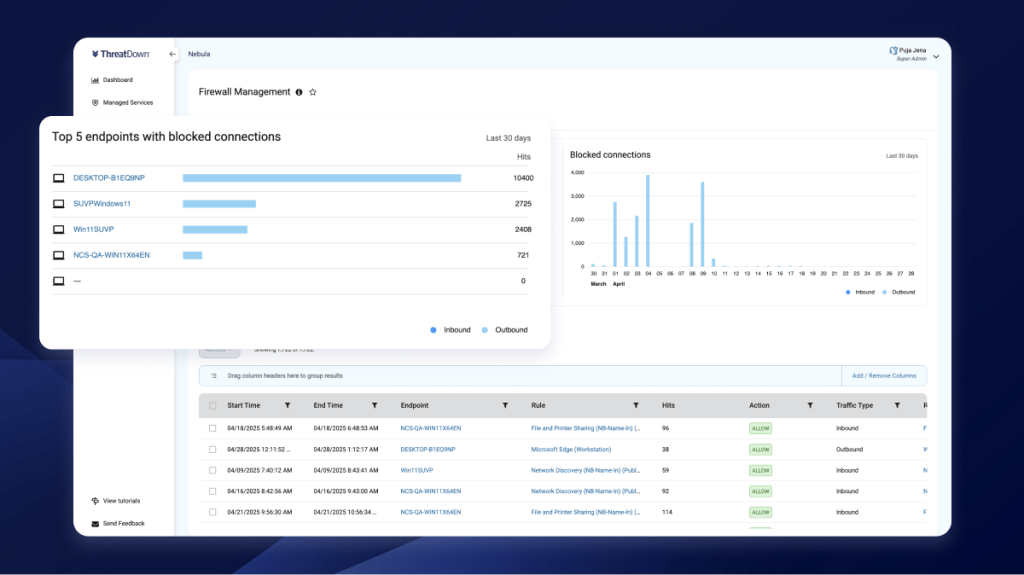
In today’s fast-paced digital world, protecting your company’s network isn’t just important, it’s absolutely critical. Cyberthreats are evolving faster than ever, and even the most vigilant IT teams can struggle to keep up. That’s why the ability to auto-isolate a machine showing critical suspicious activity is a true game-changer for business security.
Imagine this: your security solution detects a device behaving in an unusual, unexpected way. Maybe it’s trying to access sensitive data it shouldn’t, or perhaps it’s communicating with a suspicious external server. Instead of waiting for a security analyst to manually intervene, which could take precious minutes or even hours, the system instantly isolates that machine from the network. This automatic action contains threats, stopping them from spreading, preventing potential damage, data breaches, or costly downtime.
Instant protection, around the clock
One of the biggest advantages of auto-isolation is that it works 24/7, without any delay. Cyberattacks don’t follow business hours, so your defense shouldn’t either. With auto-isolation, suspicious activity triggers immediate containment, even at times your security team is off the clock. This means threats can be neutralized before they spread, keeping your entire network safer.
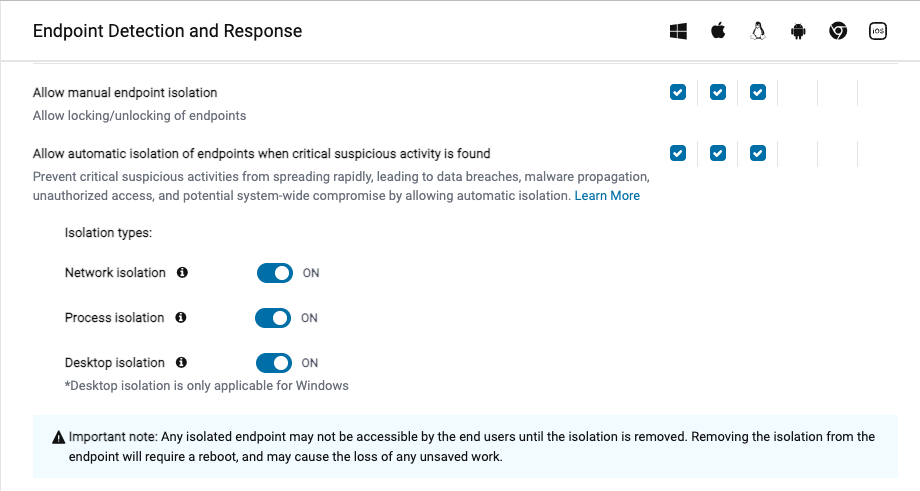
Three methods of isolation
- Network isolation: limit the device’s communications and stop malware from phoning home or spreading to other devices.
- Process isolation: halt malware and maintain employee productivity.
- Desktop isolation: block access logins and keep devices online for analysis.
Empower your security team
Auto-isolation doesn’t replace your IT experts, it empowers them. By automatically handling the most urgent threats, it frees your team to focus on deeper investigations and strategic defenses. Instead of playing whack-a-mole to isolate compromised devices manually, they can spend more time strengthening your overall security posture and responding to complex incidents.
Minimize business disruption
When a machine is compromised, every second counts. Auto-isolation helps minimize disruption by quickly cutting off the affected device, so the rest of your network stays up-and-running smoothly. This targeted approach reduces downtime and keeps your business moving forward, even in the face of a cyberattack.
Build trust with confidence
In a world where data breaches make headlines every single day, demonstrating your commitment to security is essential. Auto-isolation shows clients, partners, and employees that you take threats seriously and that you have cutting-edge defenses in place. It’s not just about protecting data, it’s about protecting your company’s reputation and future.
In short, auto-isolation is like having a vigilant digital guardian that never sleeps. An extra defender, instantly stepping in to stop threats and keep your business safe. Ready to take your business’ security to the next level? Embrace ThreatDown auto-isolation and experience peace of mind like never before.